 |
Typical financial services enterprise mitigates risk and the enormous cost of downtime and degrades service through a multiple security domain approach, where each domain is typically discrete, separated from the other domains. This approach has been adopted to prevent costly outages in one domain from impacting other services or propagating to the entire enterprise, vendors, partners and customers. Downtime and degraded service can be caused by network equipment, applications, servers, service providers and security breaches.
|
|
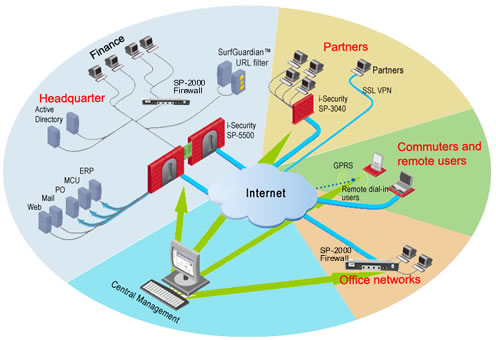
There are four primary sources of security threats for a financial services network :
- Attachment to the global Internet - while required for research as well as customer access, the global Internet posses the most likely source of attack from external sources. Also, 19% of downtime and degraded service is caused by problems at financial services organizations'
- Malicious employee - either disgruntled or motivated by profit, the internal attacker is a serious threat to the firm.
- Unknowingly malicious employee - a good employee accidentally takes an action which unknowingly compromises his computer. For example, the employee takes his laptop home, connects to the Internet, unknowingly downloads a Trojan or key logger, and returns to the office the next day, providing a remote hacker free reign of the network.
- Directly connected partner, third-party company, vendor or consultant - a trusted third party that is unknowingly compromised, or unable to contain an exploit that has affected its systems. i-Security offers security products to address all of these threats, as well as solutions to mitigate downtime caused by servers, applications, and service providers. Furthermore, high availability and high performance are hallmarks of all Juniper Networks networking equipment.
The internet perimeter provided by the Internet Access domain is primarily focused on filtering communications originating from inside the Enterprise Internal Network and Secure Server Area. In order to filter outbound communication from the organization to the global internet, the Internet Access domain is employed differently in financial services firms than most other enterprises. While the Access Network domain is responsible for access into the firm, the Internet Access domain is responsible for connecting with and securing a fairly small number of protocols and servers.
Due to the sensitivity of data and directional restrictions of data flow, typical traffic in this domain is initiated by users inside the Enterprise Internal Network, mostly using IETF standard protocols such as HTTP, HTTPS or FTP. Another widely used protocol would be streaming media protocols such as real-audio and Microsoft Streaming Media as a result of employees viewing webcasts.
For many firms, the protection offered by i-Security SP-4060 and SP-5600 with Application Intelligence enabled is sufficient. Application Intelligence provides application aware firewall for the most common IP protocols, namely HTTP, FTP, ICMP, DNS and SMTP/POP.
Of course, NAT and the ability to seamlessly integrate into the network, either via Transparent Mode or with a dynamic routing protocol, such as BGP-4 is imperative. Depending on the number of employees accessing the Internet from within the enterprise, the session setup rate may be a factor in the firewall selection. The need for IPSec or other tunneling technology is minimized in this domain, since IPSec tunnel termination is a function of the Access Network.
For advanced security, such as URL content filtering, Instant Message protecting, a SurfGuardian product can augment the firewall and provide compliance with various government regulations and corporate policy.
|
|